How to Block IP Addresses in Windows Server 2003
If you want to block an IP address or a range of IP addresses, and you don't have access to the router or firewall of the network you could use Windows' IP Security Policy Management instead. Follow the steps bellow to learn how to do so:
- Open the Run dialog box by selecting it from the Start menu or pressing WinKey and R.
- Type mmc and press OK.
- In the console select Add/Remove Snap-in from the File menu and click the Add button in the Standalone tab.
- In the Add Standalone Snap-in dialog box select IP Security Policy Management and click Add.
- In the Select Computer or Domain dialog box select Local Computer and click Finish.
- Now just close the Add Standalone Snap-in and Add/Remove Snap-in dialog boxes by clicking the Close and OK buttons respectively.
- You should now be back to the console. In the left frame right click IP Security Policies on Local Computer and select Create IP Security Policy.
- Click Next and in the Name textbox give the policy a descriptive name. The Description textbox is optional.
- Click Next, leave Activate the default response rule checkbox ticked and click Next again.
- Leave the Edit Properties checkbox ticked and click Finish.
- The Properties dialog box should be open now. Click Add button and click Next in the wizard.
- Leave This rule does not specify a tunnel selected and click Next.
- Leave All network connections selected and click Next.
- You should now see the IP Filter List step of the wizard. You need to create a new filter, so don't select any of the default ones, just click Add.
- Type a descriptive name for the filter list. The Description textbox is optional.
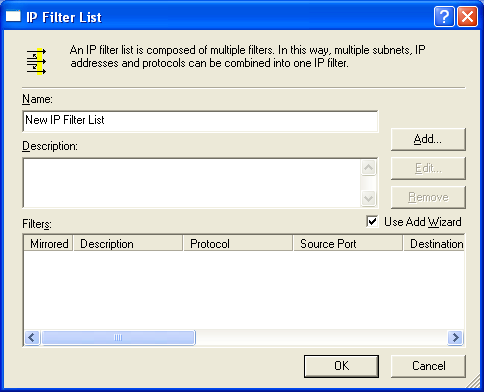
- Click Add again to start yet another wizard that will create a filter and add it to the list. Click Next.
- Leave the IP Traffic Source to My IP Address and click Next.
- For the IP Traffic Destination you could choose A specific IP Address or A specific IP Subnet to block an IP address or a range of IP address.
- Enter the IP address you would like to block and the Subnet mask if you selected A specific IP Subnet. Then click Next.
- Leave the protocol type as Any and click Next then Finish.
You now have the IP or a range of IPs blocked from accessing any service the local computer provides.